Hi everyone,
As I write this we’re entering the fifth(!) week of lockdown, and if you’re like me, you’re starting to find Zoom to be a little boring. We all know the regular tricks; tidying one corner of the room so your background appears spotless, holding up the cat for admiration, and wishing that it was illegal for someone to eat without muting their mic. To help you engage with each other, ITS has made the Snap Camera application available for installation via Software Center on your University Windows PC or laptop.
Snap camera is a fun tool that lets you change your background or yourself into some rather strange and wonderful things:

If you’d like to give this a try yourself you can now install Snap Camera on your University PC yourself. There are a few steps to follow to set everything up:
Installation
Installation is pretty easy. First, connect to the University using the Forticlient VPN application. Sign in using your regular username and password, and don’t forget the Duo authentication!
Once you’re connected, load Software Center on your computer. The easiest way is to click the magnifying glass at the bottom left and type “Software Center” into the search box. Load Software Center (remember to do this AFTER connecting to VPN).
Inside Software Center, click on Applications on the left-hand side of the Window. Find Snap Camera and install it.
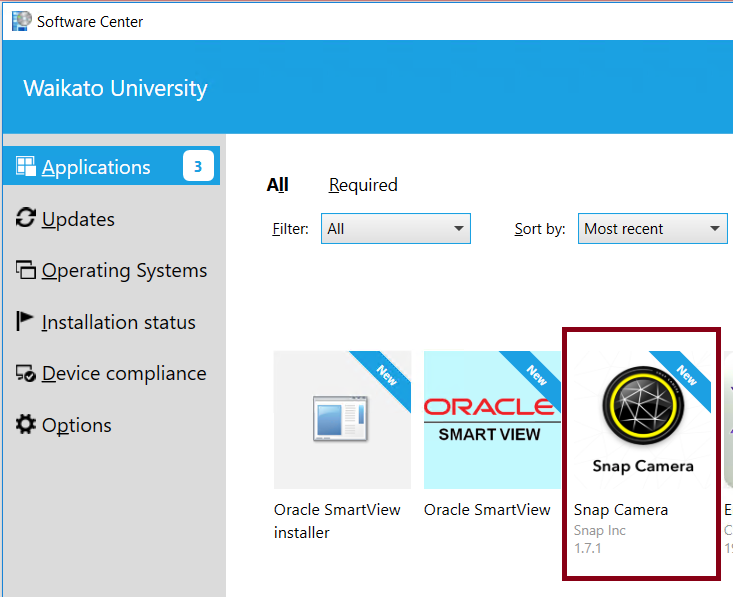
Then, restart your PC. Once you’re logged back in, it’s time to start looking for great filters for your upcoming meetings. Load your new Snap Camera application from the Start menu, and you should be able to start exploring the huge number of filters available to you. When you’ve selected the one you want to use in Zoom, follow these steps:
1. Open up Zoom on your computer and log into your account.
2. Go to Settings (the gear icon in the top right) > Video > Camera.
3. Next, select Snap Camera from the dropdown menu.
4. You should see your currently selected filter is now applied to your Zoom video.
You can only change your current Snapchat filter within the Snap Camera application on your desktop. You can’t do it directly in your Zoom meeting. So when you want something different, you can browse in the Snap Camera application. To go back to normal, just unselect the currently selected Snap filter by clicking on it again. You can change filters during the Zoom call by simply clicking a different filter inside the Snap window. It’s very easy and intuitive with a little practice.
Ngā mihi